Fortifying Digital Defense: Essential Insights into Cybersecurity—Infographic
In today’s interconnected world, cybersecurity has become a paramount concern for individuals, businesses, and governments alike. Our infographic, titled "Fortifying Digital Defense: Essential Insights into Cybersecurity," offers a comprehensive examination of the current landscape of cybersecurity, providing vital information and practical advice to help safeguard digital assets.
Common Cyber Threats
The infographic begins by outlining the most prevalent cyber threats facing users today. These include:
1. Malware
Malicious software designed to damage, disrupt, or gain unauthorized access to computer systems. Common types of malware include viruses, worms, trojans, and ransomware.
2. Phishing
Deceptive attempts to obtain sensitive information by masquerading as a trustworthy entity in electronic communications. This often involves fake emails or websites that trick users into divulging personal data.
3. Denial-of-Service (DoS) Attacks
These are cyberattacks that are aimed at making a machine or network resource unavailable to its intended users by overwhelming it with a flood of illegitimate requests.
4. Man-in-the-Middle (MitM) Attacks
Attacks where the perpetrator intercepts and possibly alters the communication between two parties who believe they are directly communicating with each other.
5. Zero-Day Exploits
Attacks that target previously unknown vulnerabilities in software or hardware, leaving no time for the developers to issue patches or updates.
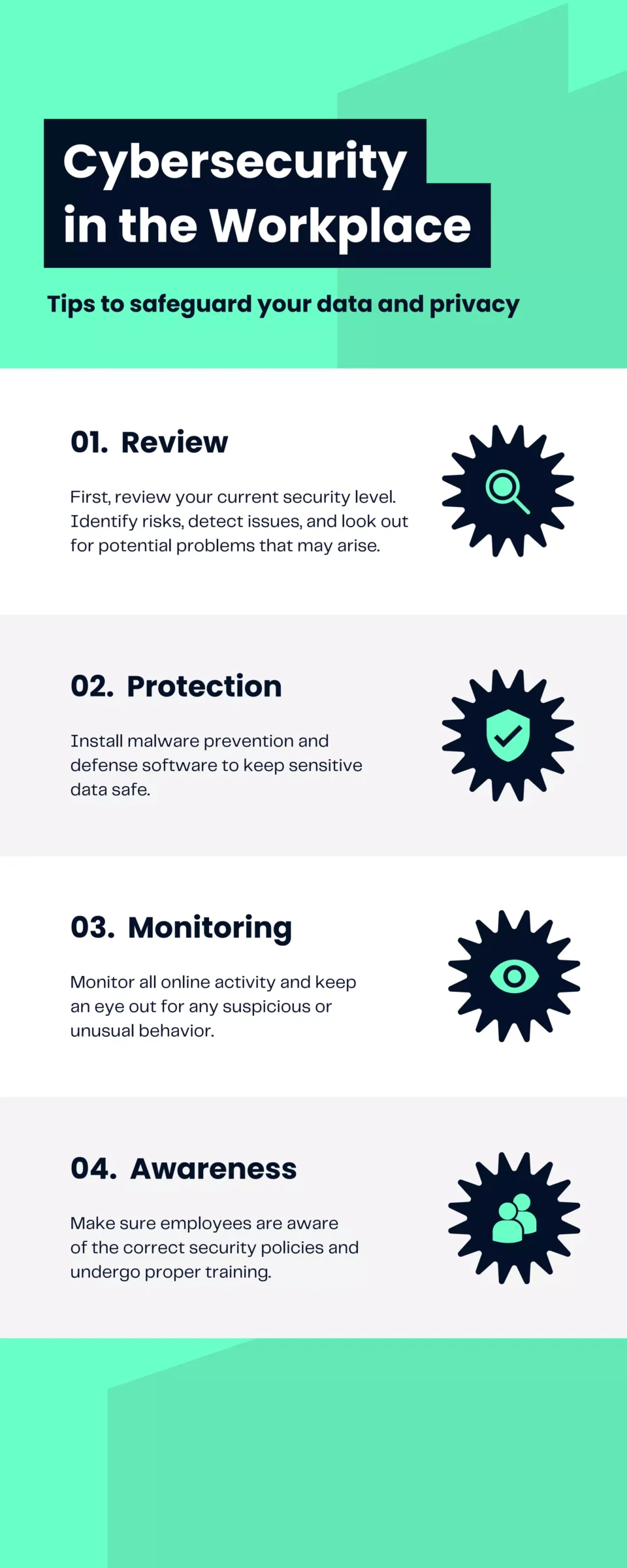
Best Practices For Protection And Cybersecurity
To combat these threats, the infographic highlights essential best practices for cybersecurity:
- Strong Passwords
Use complex, unique passwords for different accounts and change them regularly. Consider using a password manager to keep track of them securely. - Two-Factor Authentication (2FA)
Add an extra layer of security by requiring a second form of verification in addition to a password. - Regular Updates
Keep all software, including operating systems and applications, up to date to protect against the latest vulnerabilities. - Backup Data
Regularly back up important data to secure locations to prevent loss in case of an attack or hardware failure. - Awareness and Training
Educate yourself and your team about common cyber threats and how to recognize them. Regular training can significantly reduce the risk of falling victim to attacks.
The Impact Of Breaches
The infographic also delves into the profound impact cyber breaches can have on individuals and organizations. These consequences include:
1. Financial Loss
Cyberattacks can lead to significant financial losses due to fraud, theft of money, and the cost of repairing damaged systems and restoring data.
2. Reputational Damage
Breaches can severely damage the reputation of a business, leading to loss of customer trust and potentially resulting in a decline in revenue.
3. Legal and Regulatory Consequences
Organizations may face legal action and fines if they fail to protect sensitive data adequately, particularly under regulations such as GDPR or HIPAA.
4. Operational Disruption
Cyber incidents can disrupt normal operations, leading to downtime and lost productivity, which can be particularly damaging for critical infrastructure and essential services.



You can adjust your cookie preferences here.